
Strategy
Securing Development and Ensuring Compliance: Tips, Guidance, and Best Practices

Securing Development and Ensuring Compliance: Tips, Guidance, and Best Practices
In the ever-evolving tech landscape, where data is the new gold, safeguarding security and ensuring compliance throughout your development process is paramount. It's not just about checking boxes; it's about protecting your users, preserving your reputation, and safeguarding your business. Join us as we delve into practical tips, expert guidance, and best practices that will help you navigate this complex terrain.
Understanding Security and Compliance in Dev
Security and compliance are often mentioned in the same breath, but they're not one and the same. Think of Security as locking the doors and windows of your digital fortress, while compliance serves as the rulebook that tells you how to lock them properly. Neglecting either aspect can lead to a world of trouble.
Take a moment to think about some of the infamous data breaches in recent history. Remember Equifax? Marriott? These corporate giants fell victim to security breaches, and the fallout was colossal. Then there are the compliance slip-ups that have cost companies millions in fines and customer loyalty. But how can you ensure your company doesn't become the next headline in a data breach or compliance disaster?
Proven Strategies for Ensuring Security and Compliance
1. Conduct a Risk Assessment: Begin by identifying potential vulnerabilities, weak points, and the compliance requirements you need to meet. It's like knowing the terrain before building your fortress. More specifically, you should be doing the following:
- Identify Potential Threats : Start by identifying potential security threats. These can range from external threats like hackers and malware to internal threats such as employee negligence or unintentional data leaks. Think comprehensively about what could go wrong.
- Assess Compliance Requirements : Understand the specific compliance requirements that apply to your industry and the type of data you handle. Regulations like GDPR, HIPAA, or industry-specific standards must be followed. Ensure you have a clear understanding of what's expected and how to meet these requirements.
2. Embrace Secure Coding Practices: Securing your code is your first line of defense. Train your developers to write code with security in mind. Remember, a well-fortified castle starts with solid walls. To make sure your code is secure, follow these essential steps:
- Implement Code Review and Education: Establish a rigorous code review process within your development team. Train your development team to spot security vulnerabilities in the code they write and in their peers' code. Investing in developer education about secure coding practices is crucial.
- Leverage Security Libraries and Frameworks : Tools often come with built-in security features and can significantly reduce the risk of vulnerabilities in your code.
- Regular Code Scanning : Employ automated code scanning tools that can analyze your codebase for vulnerabilities. These tools excel at catching issues that might escape manual reviews.
3. Conduct Regular Security Testing: Think of penetration testing and vulnerability scanning as sending scouts to check for potential liabilities. Here's how you can further fortify your security:
- Penetration Testing: Conduct regular penetration testing to simulate real-world attacks on your systems. Ethical hackers attempt to exploit vulnerabilities in your application or infrastructure to identify weak points that need strengthening.
- Vulnerability Scanning: Use automated vulnerability scanning tools to continuously assess your systems for known vulnerabilities. Regular scans help you stay on top of security patches and updates.
- Bug Bounty Programs: Consider implementing a bug bounty program that encourages external security experts to find and report vulnerabilities in your systems. Rewarding ethical hackers can help uncover hidden risks.
4. Carry Out Compliance Audits: Audits are like a yearly health checkup for your business. They ensure you're following the rules. Prepare well, and the audits will be a breeze. To be more prepared, don't skip the following steps:
- Document Everything : Maintain comprehensive documentation of your security and compliance measures. Document policies, procedures, and technical controls. Clear documentation will be invaluable during audits.
- Conduct Mock Audits : Internal or third-party mock audits help identify and rectify compliance gaps before the real audit. Mock audits are a strategic step in preparing effectively and reducing the chances of non-compliance findings.
- Implement Continuous Monitoring: Continuous monitoring solutions can track your compliance posture in real-time. This way, you're not just preparing for audits periodically but maintaining compliance consistently.
5. Secure DevOps Practices: DevOps is all about collaboration and automation. DevSecOps is the way to go—integrate security and compliance into your development pipeline seamlessly.
- Shift-Left Security : Incorporate security considerations into every stage of your development process. This means security is not an afterthought but is integrated from the initial design phase.
- Automation : Automate security checks and compliance verification as part of your CI/CD pipeline. Automated testing and analysis tools can identify issues early in the development process, reducing the risk of vulnerabilities making it into production.
- Cross-Functional Teams : Encourage collaboration between development, operations, and security teams. When all teams work together, it's easier to ensure that security and compliance requirements are met without causing friction in the development process.
But security it's not just about having the right policies and tools in place; it's about fostering a mindset that values security and compliance as fundamental pillars of your organization. This will help you transform your workplace into a fortress, where every team member is a vigilant guardian of your organization's integrity and reputation.

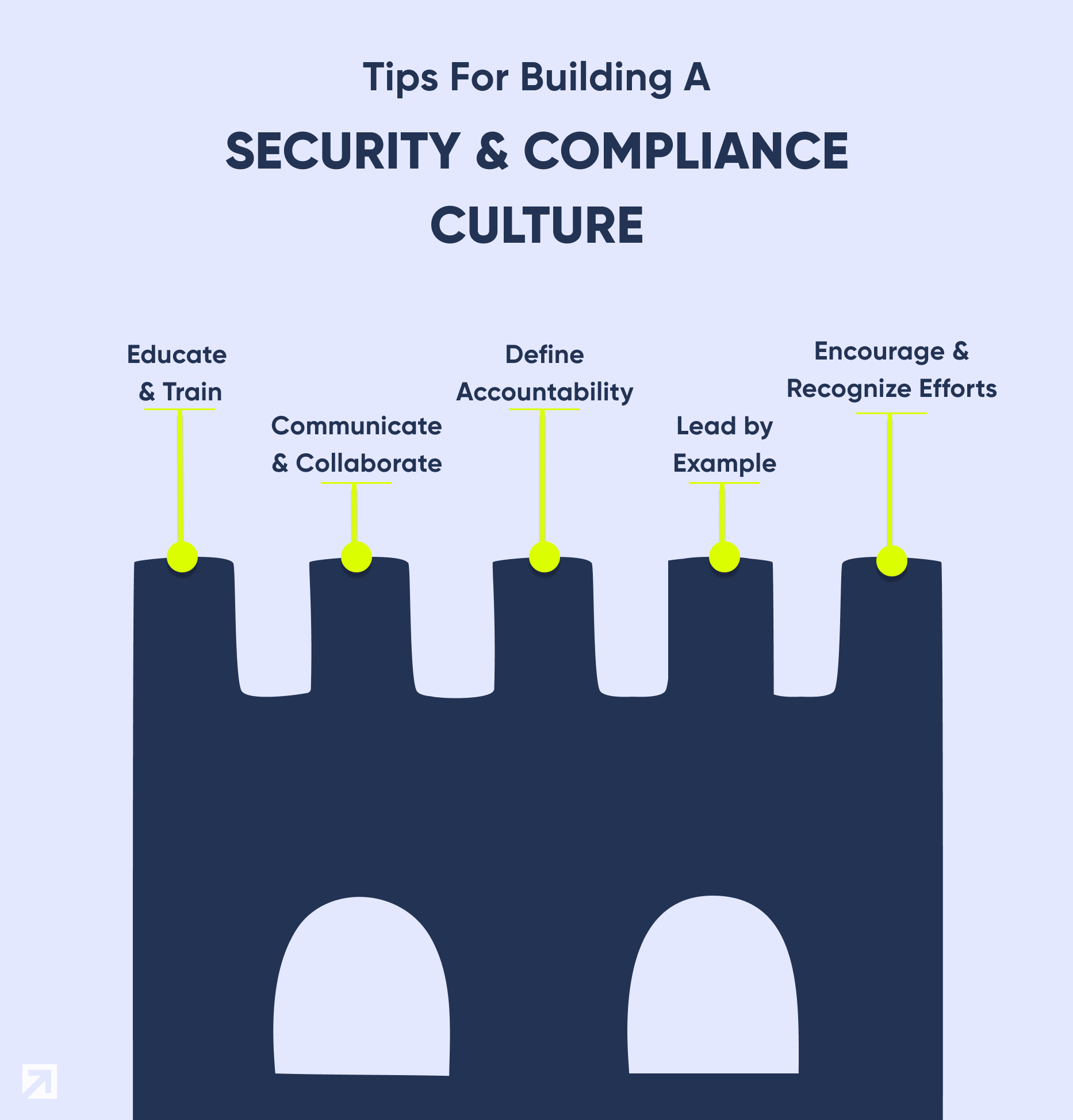
Tips for Building a Security and Compliance Culture
Educate and Train and Train:
-
Continuous Learning: A culture of security and compliance starts with education and training, which are ongoing processes. Regularly update your team on new threats, vulnerabilities, and compliance requirements. Encourage them to participate in relevant courses and certifications.
-
Customized Training: Tailor training programs to the specific needs and roles within your organization. Developers, for example, might need training on secure coding practices, while compliance officers will require in-depth knowledge of regulatory standards.
-
Simulated Phishing and Attacks: Conduct simulated phishing campaigns and cyberattack scenarios within your organization. This hands-on experience helps employees recognize and respond to threats effectively.
Communicate and Collaborate:
-
Cross-Team Collaboration: Foster collaboration between development, security, compliance, and operations teams. Break down silos by encouraging open and frequent communication. It's easier to integrate security and compliance seamlessly into the development process if these teams work together
-
Establish Clear Reporting Channels: Having clear channels for reporting security incidents or compliance concerns will ensure that employees understand the reporting process and are encouraged to report any issues without fear of retribution.
-
Regular Meetings and Updates: Schedule regular meetings and updates to discuss security and compliance matters. These forums provide opportunities for teams to share insights, progress, and challenges.
Define Accountability:
-
Define Roles and Responsibilities: Clearly define roles and responsibilities for security and compliance within your organization. Each team member should understand their part in maintaining a secure and compliant environment.
-
Performance Metrics: Establish performance metrics and key performance indicators (KPIs) related to security and compliance. Regularly review and assess performance against these metrics. Recognize and reward individuals or teams that excel in these areas.
-
Incident Response Plans: Develop and document incident response plans. Ensure that everyone knows what to do in case of a security incident or compliance violation. Regularly practice and update these plans to stay prepared.
Lead by Example:
-
Leadership Involvement: Leaders should actively participate in security and compliance initiatives. When leaders prioritize these aspects, they set a powerful example for the entire organization.
-
Consistency: Ensure that security and compliance expectations are consistently enforced from the top down. When employees see leaders taking these matters seriously, they are more likely to do the same.
-
Transparency: Leaders should be transparent about the importance of security and compliance and the potential consequences of neglecting them. This transparency builds trust and reinforces the commitment to these principles.
Encourage and Recognize Efforts:
-
Positive Reinforcement: Recognize and celebrate achievements related to security and compliance. Positive reinforcement reinforces desired behaviors and motivates teams to excel.
-
Continuous Improvement: Encourage a culture of continuous improvement. Acknowledge that security and compliance are not static goals but evolving processes that require adaptation and enhancement.
-
Feedback Mechanisms: Create feedback mechanisms that allow employees to provide suggestions and report concerns. Act on this feedback to improve security and compliance practices.
Building a security and compliance culture is an ongoing effort that requires commitment and dedication from everyone in your organization. Remember that cultural changes takes time, but the benefits in terms of reduced risk and improved compliance are well worth the investment. By prioritizing education, communication, accountability, leadership, and positive reinforcement, you can create an environment where security and compliance are not just tasks but core values.
Tools and Technologies for Enhancing Security and Compliance
There's no shortage of tools and technologies to help you on your quest for security and compliance. In this section, we'll explore the cutting-edge tools and technologies at your disposal.
| Security Tool Category | Role | Features | Benefits |
|---|---|---|---|
| Security Information and Event Management (SIEM) Systems | Real-time monitoring, alerting, and analysis of security events. |
|
|
| Intrusion Detection and Prevention Systems (IDS/IPS) | Identifying and blocking malicious activities in networks/systems. |
|
|
| Vulnerability Scanning Tools | Automatically identifying and assessing security vulnerabilities. |
|
|
| Security Orchestration, Automation, and Response (SOAR) Platforms | Streamlining security operations through automation. |
|
|
| Data Loss Prevention (DLP) Solutions | Preventing unauthorized data access, sharing, or leakage. |
|
|
| Encryption Technologies | Securing data at rest and in transit. |
|
|
| Identity and Access Management (IAM) Systems | Managing user identities, authentication, and access. |
|
|
| Security Assessment and Compliance Tools | Evaluating security posture and compliance status. |
|
|
TL;DR: Download the tool's table here and speed up your search for the perfect fit for your company.
Implementing and integrating these tools and technologies into your development and IT infrastructure can significantly enhance your ability to maintain security and compliance. However, remember that technology is just one piece of the puzzle; it must be complemented by the right processes and a culture of vigilance to be truly effective.
Top 10 Challenges and Common Pitfalls in Security & Compliance
We're not here to paint a rosy picture. Challenges are part of the journey. But with the right mindset, preparation, and guidance, you can overcome them. Here are some challenges and pitfalls to be aware of.
1. Complexity of Regulatory Landscape: The regulatory environment is constantly evolving, and it can be exceptionally complex, with a multitude of industry-specific standards and global regulations. Keeping up with these changes can be overwhelming, butailing to stay informed about the latest compliance requirements can lead to inadvertent violations, potentially resulting in severe fines and reputational damage.
2. Balancing Security and Development Speed: Development teams often face pressure to deliver products quickly. Balancing the need for rapid development with robust security measures can be challenging. Prioritizing speed over security can lead to the release of vulnerable software, making it easier for cybercriminals to exploit weaknesses.
3. Lack of Collaboration: Siloed teams and lack of collaboration between development, security, and compliance teams can hinder the implementation of security and compliance measures. When teams don't communicate effectively, security and compliance requirements may be overlooked, leading to gaps in protection and potential compliance violations.
4. Resistance to Change: Employees and teams may resist adopting new security and compliance practices, especially if they disrupt established workflows. Resistance to change can hinder the adoption of critical security measures, leaving the organization vulnerable to threats.
5. Inadequate Resources: Many organizations face resource constraints, such as budget limitations or a shortage of skilled cybersecurity professionals. Insufficient resources can result in the inability to implement and maintain necessary security and compliance measures effectively.
6. Overlooking Third-Party Risks: Organizations often rely on third-party vendors and partners for various aspects of their operations. These external relationships introduce additional security and compliance risks. Failing to thoroughly assess and monitor the security and compliance practices of third parties can expose the organization to risks beyond its control.
7. False Sense of Security: The implementation of security measures can sometimes create a false sense of security. Organizations may assume they are fully protected when vulnerabilities still exist. A false sense of security can lead to complacency and inadequate response to emerging threats.
8. Incomplete Testing and Validation: Rigorous testing and validation of security and compliance measures are essential, but they can be time-consuming and resource-intensive. Incomplete testing can lead to a failure to detect vulnerabilities or compliance gaps, leaving the organization exposed to risks.
9. Lack of User Awareness: End-users can unintentionally introduce security vulnerabilities through actions like clicking on phishing emails or using weak passwords. Neglecting user awareness training can undermine the most robust security measures, as human error remains a significant risk factor.
10. Focusing Solely on Technology: Organizations often emphasize technology solutions while neglecting the importance of a security-aware culture and well-defined processes. Overreliance on technology can lead to overlooking human and procedural aspects of security and compliance, which are equally crucial.
Conclusions
The journey to safeguarding security and compliance in the tech landscape is a perpetual commitment that demands constant dedication.
As you navigate these complexities, remember that at Xmartlabs, we take your security and compliance seriously. Our team of experts is here to ensure that your software not only meets but exceeds the stringent standards of data protection and regulatory compliance.
We're your trusted partner in building software solutions that allow you to focus on what truly matters, free from worries about vulnerabilities or non-compliance. Contact us today!

